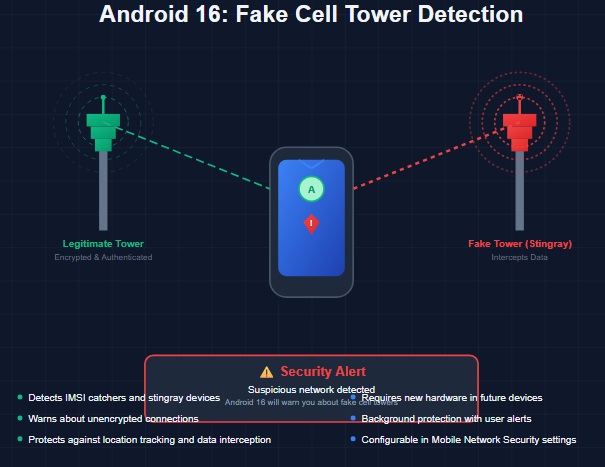
📱🔒 Google is taking mobile security to a whole new level. With the upcoming Android 16 update, your smartphone will soon be able to detect fake cellular towers—a major step forward in protecting users from potential surveillance and data interception threats.
🛰️ What Are Fake Cell Towers?
Also known as IMSI catchers or stingrays, fake base stations impersonate legitimate mobile network towers. Their purpose? To trick your phone into connecting to them, allowing attackers to intercept your calls, texts, location data, or even inject malware. These are often used in sophisticated cyberattacks and surveillance operations.
While detection and mitigation of IMSI catchers have long been discussed in telecom circles, most smartphones until now had no native protection against them—leaving users unaware and vulnerable.
🆕 What’s New in Android 16?
According to the Android 16 Developer Preview, Google is introducing a new alert system that will notify users when:
-
Their device is connected to a non-encrypted cellular network
-
The network appears to be anomalous or possibly malicious
-
There’s a potential man-in-the-middle (MITM) attack taking place
This feature is being integrated as part of the “Cellular Security” alerts within the operating system and will include warnings such as:
“Mobile network may be monitored”
or
“Connected to a fake base station”
This level of visibility is a first for Android, and it mirrors Google’s ongoing investment in user privacy and threat detection across the Android ecosystem.
🔐 Why It Matters
Mobile networks have evolved significantly, especially with 5G deployments. But legacy vulnerabilities—particularly those affecting 2G and 3G fallback mechanisms—still pose security risks. Malicious actors can force devices to downgrade to older generations that lack encryption, making it easier to intercept data.
Google already introduced an option to disable 2G connectivity in Android 14, and now Android 16 goes further by actively detecting suspicious behavior at the radio layer.
This is particularly important for:
-
Journalists
-
Activists
-
Executives or political figures
-
Enterprise users dealing with sensitive data
…and really, anyone concerned about mobile privacy.
📶 How Does It Work Technically?
The system works by detecting inconsistencies in the network’s signaling protocols. If the phone identifies:
-
An unsecured or unencrypted connection
-
A cell tower broadcasting suspicious parameters
-
Abnormal changes in network identity (like MCC/MNC)
…then the alert is triggered. These detections rely on advancements in the Radio Interface Layer (RIL) and underlying modem firmware, suggesting that not all devices may be compatible unless their chipsets support such detection.
📱 Will Your Phone Support It?
The feature is expected to roll out first on Pixel devices during the beta phase of Android 16, with broader support depending on OEM implementation and modem capabilities. It’s likely that high-end models from Samsung, Xiaomi, and others will support this as part of their next-gen devices.
🌐 Telecom Implications
For telecom professionals, this update could impact how operator trust and network quality assurance are handled. Operators may need to ensure stronger authentication and encryption enforcement at the RAN level to avoid false flags.
It’s also a call to accelerate 2G sunset plans, as unencrypted legacy networks continue to be an attack vector.
🧠 Final Thoughts
With Android 16, mobile cybersecurity takes a major leap. By empowering users to detect fake cell towers and network tampering in real-time, Google is not only responding to emerging threats—but setting a new standard for mobile OS-level protection.
If you work in telecom, security, or network architecture, keep an eye on this evolution—it’s a sign of the increasing convergence between device-level intelligence and network integrity.
Don’t miss our 5G Security Training to learn more about the last security updates.
Benefit from Massive discount on our 5G Training with 5WorldPro.com
Start your 5G journey and obtain 5G certification
contact us: contact@5GWorldPro.com