5G introduces new architectures, services, and technologies to meet the increasingly stringent requirements on experience and applications. However, these additions also bring with them new security challenges. For example, the new software architecture has its own security requirements in aspects such as slice security protection and multi-slice risk management. In terms of new services, 5G networks need to support applications with enhanced security capabilities to meet the security requirements of vertical industries. And in terms of new technologies, 5G networks must consider the future impact of technologies, such as quantum computing, on traditional cryptographic algorithms.
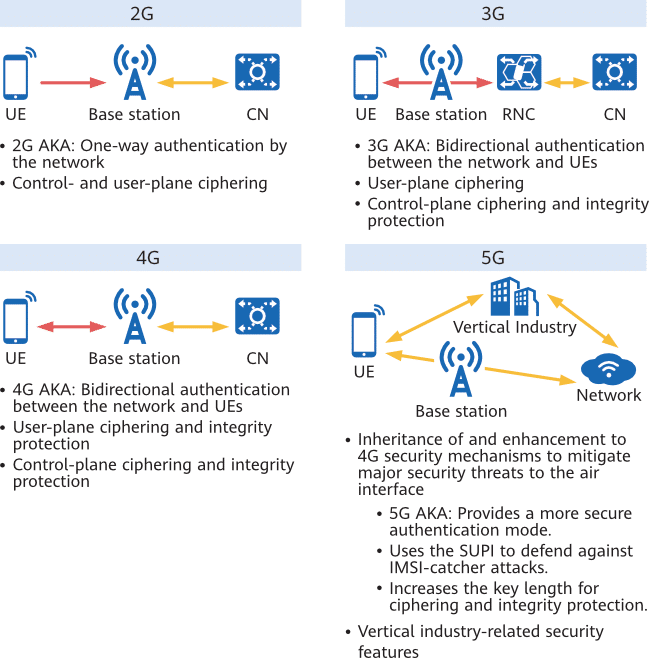
As the successor of 4G networks, 5G needs to be able to handle new security challenges while maintaining the same security capabilities as 4G. For this purpose, 3GPP specifications enable 5G to inherit and enhance the security mechanisms of 4G as well as provide additional security features for 5G applications in vertical industries. This is explained in more detail in 3 Security Threats to the 5G Air Interface and Corresponding Countermeasures and 4 5G Security Features for Vertical Industries.
In addition, unified and continuously evolving security assessment standards are required for 5G networks, in turn facilitating improvements in security levels across the mobile industry. 5 Wireless Network Equipment Security Certification introduces the industry’s most recognized standards and specifications for equipment security assessment.
3 Security Threats to the 5G Air Interface and Corresponding Countermeasures
The main security threats to the air interface are the same between 4G and 5G. To cope with these threats, 5G uses the same security mechanisms as 4G and makes some additional enhancements. Figure 3-1 shows the major security threats to the 5G air interface.
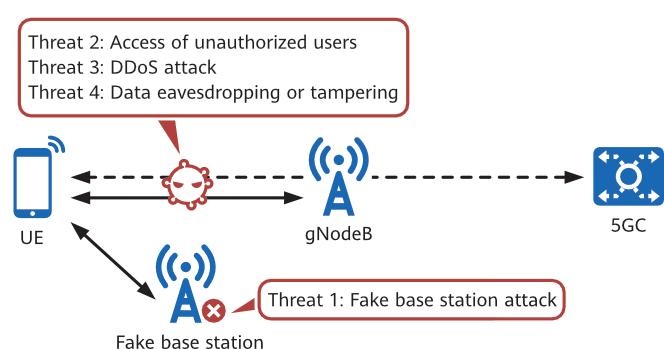
Fake Base Station Attack
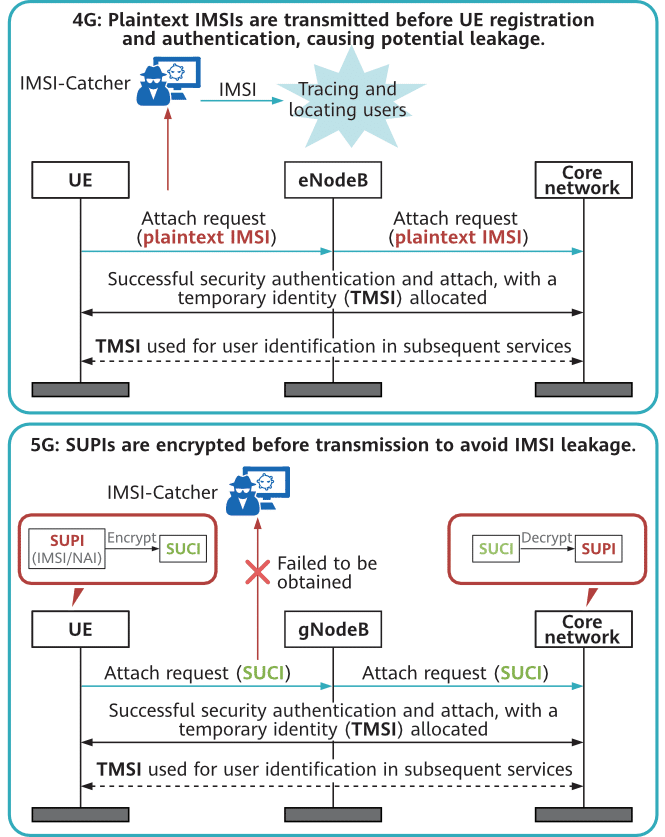
On 2G, 3G, and 4G networks, an international mobile subscriber identity (IMSI) is used to uniquely identify a mobile subscriber or UE. An IMSI is a permanent identity of a subscriber. IMSIs are transmitted in plaintext on 2G, 3G, and 4G networks and can be obtained in attacks launched by devices such as an IMSI-catcher, leading to subscriber identity disclosure. An attacker, with an IMSI obtained in advance, can use a fake base station to forge a signaling message and determine whether the UE is near the fake base station based on the response from the UE. In this way, the attacker can illegally trace the UE location.
5G networks use a subscription permanent identifier (SUPI), which consists of an IMSI or network access identifier (NAI), to uniquely identify a mobile subscriber or UE. A SUPI is encrypted into a Subscription Concealed Identifier (SUCI) for transmission to defend against IMSI-catcher attacks by fake base stations.
Access of Unauthorized Users
Unauthorized users using unauthenticated UEs to access the network will consume network resources. If an attacker uses a large number of unauthorized UEs to launch an attack against the network, severe accidents such as network congestion, denial of service, and network device faults may occur.
Both 5G and 4G support two-way authentication between UEs and the network. However, 5G provides a unified authentication architecture for 3GPP and non-3GPP authentication to adapt to different UE types and network access types. In addition, 5G uses better authentication modes to improve air interface access security.
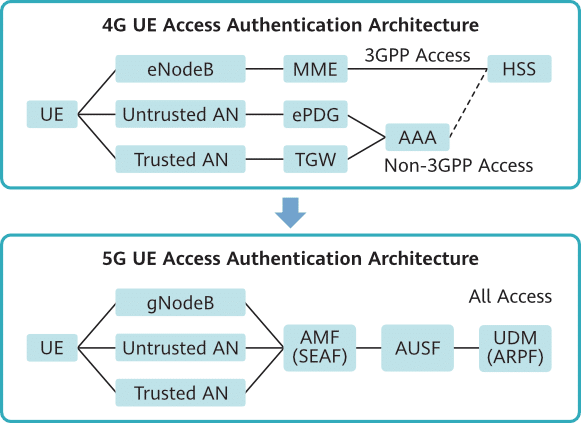
5G authentication-related network functions (NFs) are as follows:
- Unified data management (UDM) and Authentication Credential Repository and Processing Function (ARPF): The UDM and ARPF are co-deployed. The co-deployed node generates 5G authentication parameters and vectors based on the stored subscriber root keys and authentication-related subscription data.
- Authentication server function (AUSF): The AUSF selects an authentication mode based on the network access type.
- Access and mobility management function (AMF) and Security Anchor Function (SEAF): The AMF and SEAF are co-deployed. The co-deployed node derives lower-layer keys based on the anchor key and confirms the serving network authentication result in 5G Authentication and Key Agreement (AKA) authentication mode.
Table 3-1 Differences between 4G and 5G authentication modes
|
Network Access Type |
4G Authentication Mode |
5G Authentication Mode |
Description |
|---|---|---|---|
|
3GPP |
EPS AKA |
EAP-AKA‘, 5G AKA |
Compared with EPS-AKA, EAP-AKA‘ changes the authentication vector from a quadruple to a quintuple. The improved security level makes subscriber authentication data safer. Compared with EPS AKA, 5G AKA:
|
|
Non-3GPP |
EAP-AKA, EAP-AKA‘ |
EAP-AKA‘ |
Compared with EAP-AKA, EAP-AKA‘:
|
Don’t miss our 5G Security Training to learn more about the last updates.
Benefit from Massive discount on our 5G Training with 5WorldPro.com
Start your 5G journey and obtain 5G certification
contact us: contact@5GWorldPro.com